從安全上考慮, 現在有了一種新的 VLAN 機制,所有伺服器在同一個子網中, 但伺服器只能與自己的預設閘道器通信。此機制即為Privte VLAN (pVLAN)
pVLAN分為兩大塊 : Primary VLAN & Secondary VLAN
其中 Secondary VLAN又分為 Isolate VLAN & Community VLAN
pVLAN中也定義了三種port型式 :
Promiscous Port - A promiscuous port belongs to the primary VLAN and can communicate with all interfaces, including the community and isolated host ports that belong to the secondary VLANs associated with the primary VLAN
Isolated Port - An isolated port is a host port that belongs to an isolated secondary VLAN. It has
complete Layer 2 separation from other ports within the same private VLAN, except for the
promiscuous ports.
complete Layer 2 separation from other ports within the same private VLAN, except for the
promiscuous ports.
Community Port - A community port is a host port that belongs to a community secondary VLAN.
Community ports communicate with other ports in the same community VLAN and with
promiscuous ports
Community ports communicate with other ports in the same community VLAN and with
promiscuous ports
Configuration
第一步 Set VTP mode to transparent.
第二步 Create the primary and secondary VLANs and associate them
第三步 Configure interfaces to be isolated or community host ports, and assign VLAN membership to the host port

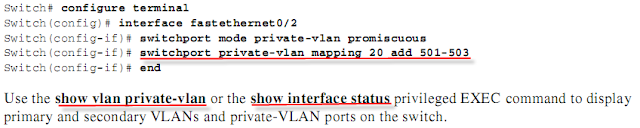
第四步 Configure interfaces as promiscuous ports, and map the promiscuous ports to the primary-secondary VLAN pair
第六步 Verify private-VLAN configuration









沒有留言:
張貼留言