轉載於 http://www.ringline.com.tw/epaper/Forum971101.htm
InServ的服務模式需要透過資源預留協議(RSVP, Resource ReSerVation Protocol)的信令協定來完成,其中必須注意RSVP的信息是單方向hop by hop建立資源預留的。RSVP主要的信息有PATH、RESV (Reservation-Request)、Error and Conformation及Teardown四種。PATH跟RESV分別是RSVP從Source端與Destination端之間傳遞hop by hop建立需求跟回應的訊息,例如[圖2],再以Error and Conformation的訊息做確認與否;Teardown的訊息為移除原先PATH或RESV的狀態之用。
圖2:RSVP PATH與RESV messages的示意圖
以[圖3]為例子,假設PC1已建立某頻寬的traffic到PC2,所走的路徑經由R1 ð R 5 ðR6 ð R3 ð R4等5個Hop Router,其中已將R6跟R3之間的頻寬耗用到只剩下6Kbps。
圖3:PC1已建立頻寬預留至PC2
當PC3預申請建立24Kbps的頻寬到PC4,所走的路徑經由R 5 ð R6 ð R3 ðR8等4個Hop Router,但是R6與R3之間的頻寬出現瓶頸已不足預留一個新的24Kbps頻寬出來,如[圖4]。故R6回傳R5時RESV時伴隨著Bandwidth unavailable的Reservation-Request error message。PC3必須放棄這條路徑,將原先的PATH及RESV的狀態Teardown,另尋建立R 5 ð R2 ð R3 ð R8的中繼站。在此可以看出RSVP的特性可允許去回不同路,因為資源的保留是針對單向而計算的。
圖4:PC3欲申請建立24Kbps的頻寬至PC4
Configuration
1. Enable RSVP
2. Enter Senders in the RSVP Database
3. Enter Receivers in the RSVP Database
4. Enter Multicast Addresses
5. Control Which RSVP Neighbor Can Offer a Reservation
6. Monitor RSVP
2009年12月31日 星期四
Private VLAN (pVLAN)
從安全上考慮, 現在有了一種新的 VLAN 機制,所有伺服器在同一個子網中, 但伺服器只能與自己的預設閘道器通信。此機制即為Privte VLAN (pVLAN)
pVLAN分為兩大塊 : Primary VLAN & Secondary VLAN
其中 Secondary VLAN又分為 Isolate VLAN & Community VLAN
pVLAN中也定義了三種port型式 :
Promiscous Port - A promiscuous port belongs to the primary VLAN and can communicate with all interfaces, including the community and isolated host ports that belong to the secondary VLANs associated with the primary VLAN
Isolated Port - An isolated port is a host port that belongs to an isolated secondary VLAN. It has
complete Layer 2 separation from other ports within the same private VLAN, except for the
promiscuous ports.
complete Layer 2 separation from other ports within the same private VLAN, except for the
promiscuous ports.
Community Port - A community port is a host port that belongs to a community secondary VLAN.
Community ports communicate with other ports in the same community VLAN and with
promiscuous ports
Community ports communicate with other ports in the same community VLAN and with
promiscuous ports
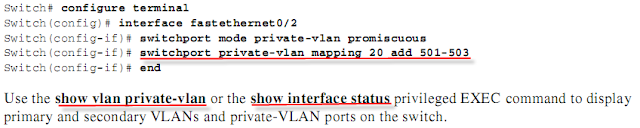
Configuration
第一步 Set VTP mode to transparent.
第二步 Create the primary and secondary VLANs and associate them
第三步 Configure interfaces to be isolated or community host ports, and assign VLAN membership to the host port

第四步 Configure interfaces as promiscuous ports, and map the promiscuous ports to the primary-secondary VLAN pair
第六步 Verify private-VLAN configuration
2009年12月30日 星期三
Switched Port Analyzer (SPAN)
Switched Port Analyzer
SPAN(Switched Port Analyzer)——用於交換環境的性能管理和排錯。
SPAN 能夠將某個 VLAN 或一組埠(源)的網路流量複製到某個埠中(目的),而那個目的埠通常連接到網路分析器(比如,SwitchProbe 設備)。SPAN不會對源埠或 VLAN 的網路流量交換產生影響。
SPAN分為兩種
1. Local SPAN
2. Remote SPAN
--------------------------------------------------------------------------------------------------------------------------------------
• The switch supports up to two source sessions (local SPAN and RSPAN source sessions). You can run both a local SPAN and an RSPAN source session in the same switch. The switch supports a total of 66 source and RSPAN destination sessions.
• You can have multiple destination ports in a SPAN session, but no more than 64 destination ports.
• You can configure two separate SPAN or RSPAN source sessions with separate or overlapping sets of SPAN source ports and VLANs. Both switched and routed ports can be configured as SPAN sources and destinations.
• SPAN sessions do not interfere with the normal operation of the switch. However, an oversubscribed SPAN destination, for example, a 10-Mb/s port monitoring a 100-Mb/s port, can result in dropped or lost packets.
• When RSPAN is enabled, each packet being monitored is transmitted twice, once as normal traffic and once as a monitored packet. Therefore monitoring a large number of ports or VLANs could potentially generate large amounts of network traffic.
• You can configure SPAN sessions on disabled ports; however, a SPAN session does not become active unless you enable the destination port and at least one source port or VLAN for that session.
• The switch does not support a combination of local SPAN and RSPAN in a single session. That is, an RSPAN source session cannot have a local destination port, an RSPAN destination session cannot have a local source port, and an RSPAN destination session and an RSPAN source session that are using the same RSPAN VLAN cannot run on the same switch.
--------------------------------------------------------------------------------------------------------------------------------------
The goal of receive (or ingress) SPAN is to monitor as much as possible all the packets received by the source interface or VLAN before any modification or processing is performed by the switch. A copy of each packet received by the source is sent to the destination port for that SPAN session.
Transmit (Tx) SPAN—
The goal of transmit (or egress) SPAN is to monitor as much as possible all
the packets sent by the source interface after all modification and processing is performed by the switch. A copy of each packet sent by the source is sent to the destination port for that SPAN session. The copy is provided after the packet is modified.
Both—
In a SPAN session, you can also monitor a port or VLAN for both received and sent packets. This is the default.
The default configuration for local SPAN session ports is to send all packets untagged. SPAN also does not normally monitor bridge protocol data unit (BPDU) packets and Layer 2 protocols, such as Cisco Discovery Protocol (CDP), VLAN Trunk Protocol (VTP), Dynamic Trunking Protocol (DTP), Spanning Tree Protocol (STP), and Port Aggregation Protocol (PAgP). However, when you enter the encapsulation replicate keywords when configuring a destination port, these changes occur:
• Packets are sent on the destination port with the same encapsulation—untagged, Inter-Switch Link (ISL), or IEEE 802.1Q—that they had on the source port.
• Packets of all types, including BPDU and Layer 2 protocol packets, are monitored.
-------------------------------------------------------------------------------------------------------------------------------------
A destination port does not participate in STP while its SPAN or RSPAN session is active. The destination port can participate in STP after the SPAN or RSPAN session is disabled. On a source port, SPAN does not affect the STP status. STP can be active on trunk ports carrying an RSPAN VLAN.
CDP
A SPAN destination port does not participate in CDP while the SPAN session is active. After the SPAN session is disabled, the port again participates in CDP.
VTP
You can use VTP to prune an RSPAN VLAN between switches.
EtherChannel
You can configure an EtherChannel group as a source port but not as a SPAN destination port. When a group is configured as a SPAN source, the entire group is monitored.
Multicast
Multicast traffic can be monitored. For egress and ingress port monitoring, only a single unedited packet is sent to the SPAN destination port. It does not reflect the number of times the multicast packet is sent.
A private-VLAN port cannot be a SPAN destination port.
A secure port cannot be a SPAN destination port.
An IEEE 802.1x port can be a SPAN source port.
You can enable IEEE 802.1x on a port that is a SPAN destination port; however, IEEE 802.1x is disabled until the port is removed as a SPAN destination.
------------------------------------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------------------------------------
1.創建RSPAN 專用的VLAN:
SW(config)#vlan {vlan-id}
2.定義該VLAN為RSPAN VLAN:
SW (config-vlan)#remote-span
3.定義源交換機的源埠.對於Catalyst 3550交換機,會話數隻支援兩條,即1和2,還可以定義監聽流量的方向,默認監聽雙向流量:
SW (config)#monitor session {session-number} source {interface interface|vlan vlan-id} [rx|tx|both]
4.定義源交換機的目標埠:
SW (config)#monitor session {session-number} destination remote vlan {rspan-vlan-id}
5.定義目標交換機的源埠:
SW (config)#monitor session {session-number} source remote vlan {rspan-vlan-id}
6.定義目標交換機的目標埠:
SW (config)#monitor session {session-number} destination {interface interface|vlan vlan-id} [rx|tx|both]
SPAN(Switched Port Analyzer)——用於交換環境的性能管理和排錯。
SPAN 能夠將某個 VLAN 或一組埠(源)的網路流量複製到某個埠中(目的),而那個目的埠通常連接到網路分析器(比如,SwitchProbe 設備)。SPAN不會對源埠或 VLAN 的網路流量交換產生影響。
SPAN分為兩種
1. Local SPAN
2. Remote SPAN
Local SPAN
Local SPAN supports a SPAN session entirely within one switch; all source ports or source VLANs and destination ports are in the same switch. Local SPAN copies traffic from one or more source ports in any VLAN or from one or more VLANs to a destination port for analysisRSPAN
RSPAN supports source ports, source VLANs, and destination ports on different switches, enabling remote monitoring of multiple switches across your network.--------------------------------------------------------------------------------------------------------------------------------------
Traffic monitoring in a SPAN session has these restrictions:
• Sources can be ports or VLANs, but you cannot mix source ports and source VLANs in the same session.• The switch supports up to two source sessions (local SPAN and RSPAN source sessions). You can run both a local SPAN and an RSPAN source session in the same switch. The switch supports a total of 66 source and RSPAN destination sessions.
• You can have multiple destination ports in a SPAN session, but no more than 64 destination ports.
• You can configure two separate SPAN or RSPAN source sessions with separate or overlapping sets of SPAN source ports and VLANs. Both switched and routed ports can be configured as SPAN sources and destinations.
• SPAN sessions do not interfere with the normal operation of the switch. However, an oversubscribed SPAN destination, for example, a 10-Mb/s port monitoring a 100-Mb/s port, can result in dropped or lost packets.
• When RSPAN is enabled, each packet being monitored is transmitted twice, once as normal traffic and once as a monitored packet. Therefore monitoring a large number of ports or VLANs could potentially generate large amounts of network traffic.
• You can configure SPAN sessions on disabled ports; however, a SPAN session does not become active unless you enable the destination port and at least one source port or VLAN for that session.
• The switch does not support a combination of local SPAN and RSPAN in a single session. That is, an RSPAN source session cannot have a local destination port, an RSPAN destination session cannot have a local source port, and an RSPAN destination session and an RSPAN source session that are using the same RSPAN VLAN cannot run on the same switch.
--------------------------------------------------------------------------------------------------------------------------------------
SPAN sessions can monitor these traffic types:
Receive (Rx) SPAN—The goal of receive (or ingress) SPAN is to monitor as much as possible all the packets received by the source interface or VLAN before any modification or processing is performed by the switch. A copy of each packet received by the source is sent to the destination port for that SPAN session.
Transmit (Tx) SPAN—
The goal of transmit (or egress) SPAN is to monitor as much as possible all
the packets sent by the source interface after all modification and processing is performed by the switch. A copy of each packet sent by the source is sent to the destination port for that SPAN session. The copy is provided after the packet is modified.
Both—
In a SPAN session, you can also monitor a port or VLAN for both received and sent packets. This is the default.
The default configuration for local SPAN session ports is to send all packets untagged. SPAN also does not normally monitor bridge protocol data unit (BPDU) packets and Layer 2 protocols, such as Cisco Discovery Protocol (CDP), VLAN Trunk Protocol (VTP), Dynamic Trunking Protocol (DTP), Spanning Tree Protocol (STP), and Port Aggregation Protocol (PAgP). However, when you enter the encapsulation replicate keywords when configuring a destination port, these changes occur:
• Packets are sent on the destination port with the same encapsulation—untagged, Inter-Switch Link (ISL), or IEEE 802.1Q—that they had on the source port.
• Packets of all types, including BPDU and Layer 2 protocol packets, are monitored.
-------------------------------------------------------------------------------------------------------------------------------------
SPAN interacts with these features
STPA destination port does not participate in STP while its SPAN or RSPAN session is active. The destination port can participate in STP after the SPAN or RSPAN session is disabled. On a source port, SPAN does not affect the STP status. STP can be active on trunk ports carrying an RSPAN VLAN.
CDP
A SPAN destination port does not participate in CDP while the SPAN session is active. After the SPAN session is disabled, the port again participates in CDP.
VTP
You can use VTP to prune an RSPAN VLAN between switches.
EtherChannel
You can configure an EtherChannel group as a source port but not as a SPAN destination port. When a group is configured as a SPAN source, the entire group is monitored.
Multicast
Multicast traffic can be monitored. For egress and ingress port monitoring, only a single unedited packet is sent to the SPAN destination port. It does not reflect the number of times the multicast packet is sent.
A private-VLAN port cannot be a SPAN destination port.
A secure port cannot be a SPAN destination port.
An IEEE 802.1x port can be a SPAN source port.
You can enable IEEE 802.1x on a port that is a SPAN destination port; however, IEEE 802.1x is disabled until the port is removed as a SPAN destination.
------------------------------------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------------------------------------
Configuration
SPAN
RSPAN:
配置RSPAN的步驟如下:1.創建RSPAN 專用的VLAN:
SW(config)#vlan {vlan-id}
2.定義該VLAN為RSPAN VLAN:
SW (config-vlan)#remote-span
3.定義源交換機的源埠.對於Catalyst 3550交換機,會話數隻支援兩條,即1和2,還可以定義監聽流量的方向,默認監聽雙向流量:
SW (config)#monitor session {session-number} source {interface interface|vlan vlan-id} [rx|tx|both]
4.定義源交換機的目標埠:
SW (config)#monitor session {session-number} destination remote vlan {rspan-vlan-id}
5.定義目標交換機的源埠:
SW (config)#monitor session {session-number} source remote vlan {rspan-vlan-id}
6.定義目標交換機的目標埠:
SW (config)#monitor session {session-number} destination {interface interface|vlan vlan-id} [rx|tx|both]
why minimum Ethernet payload size is 46 bytes ?
轉載於 http://www.itechtalk.com/thread212.html
shows Ethernet Node A and Ethernet Node B at the farthest ends of a 5-4-3 network
using 10Base5 cabling.
When Node A begins transmitting, the signal must propagate the network length. In the worst-case collision scenario, Node B begins to transmit just before the signal for Node A’s frame reaches it. The collision signal of Node A and Node B’s frame must travel back to Node A for Node A to detect that a collision has occurred.
The time it takes for a signal to propagate from one end of the network to the other is known as the propagation delay. In this worst-case collision scenario, the time that it takes for Node A to detect that its frame has been collided with is twice the propagation delay. Node A’s frame must travel all the way to Node B, and then the collision signal must travel all the way from Node B back to Node A. This time is known as the slot time. An Ethernet node must be transmitting a frame for the slot time for a collision with that frame to be detected. This is the reason for the minimum Ethernet frame size. The propagation delay for this maximum-extent Ethernet network is 28.8 μs. Therefore, the slot time is 57.6 μs. To transmit for 57.6 μs with a 10 Mbps bit rate, an Ethernet node must transmit 576 bits. Therefore, the entire Ethernet frame, including the Preamble field, must be a minimum size of 576 bits, or 72 bytes long. Subtracting the Preamble (8 bytes), Source Address (6 bytes), Destination Address (6 bytes), EtherType (2 bytes), and FCS (4 bytes) fields, the minimum Ethernet payload size is 46 bytes.
shows Ethernet Node A and Ethernet Node B at the farthest ends of a 5-4-3 network
using 10Base5 cabling.
When Node A begins transmitting, the signal must propagate the network length. In the worst-case collision scenario, Node B begins to transmit just before the signal for Node A’s frame reaches it. The collision signal of Node A and Node B’s frame must travel back to Node A for Node A to detect that a collision has occurred.
The time it takes for a signal to propagate from one end of the network to the other is known as the propagation delay. In this worst-case collision scenario, the time that it takes for Node A to detect that its frame has been collided with is twice the propagation delay. Node A’s frame must travel all the way to Node B, and then the collision signal must travel all the way from Node B back to Node A. This time is known as the slot time. An Ethernet node must be transmitting a frame for the slot time for a collision with that frame to be detected. This is the reason for the minimum Ethernet frame size. The propagation delay for this maximum-extent Ethernet network is 28.8 μs. Therefore, the slot time is 57.6 μs. To transmit for 57.6 μs with a 10 Mbps bit rate, an Ethernet node must transmit 576 bits. Therefore, the entire Ethernet frame, including the Preamble field, must be a minimum size of 576 bits, or 72 bytes long. Subtracting the Preamble (8 bytes), Source Address (6 bytes), Destination Address (6 bytes), EtherType (2 bytes), and FCS (4 bytes) fields, the minimum Ethernet payload size is 46 bytes.
Ethernet Frame
In the TCP/IP world , the encapsulaton of IP datagrams is defined in RFC 894 for Ethernet and in RFC 1042 for IEEE 802 networks.
The Host Requirements RFC requires that every Internet host connected to a 10Mbits/sec Ethernet cable:
1. Must be able to send and recieve packets using RFC 894 encapsulation.
2. Should be able to recieve RFC 1042 packets intermixed with RFC 894
3. May be able to send packets using RFC1042 encapsulation. If the host can send both types of packets , the type of packets mustbe configuratble and the configuration option must default to RFC 894 packets.
- The 802 lengh field says how many bytes follow,up to but not including the CRC at end.
- The Ethernet type filed identifies the type of data that follows.
- In the 802 frame the same type filed occurs later int the SNAP(Sub-network Access Protocol)header , Fortunately none of the valid 802 lengh values is the same as Ethernet type values , making the two frame formats distinguishable.
- In the Ethernet frame the data immediately follows the type filed, while in the 802 frame format 3 Bytes of 802.2LLC and 5 bytes of 802.2 SNAP follow.
- The DSAP(Destination Service Access Point) and SSAP (Source Service Access Point) are both set to 0xAA . the control filed is set to 0×03. The next 3 bytes , the Org code are all o.
- The CRC field is a cyclic redundancy check that detects errors in the rest of the frame ( this is also called the FCS or frame check sequence)
- There is a minimum size for 802.3 and Ethernet frames. The minimun requires that the data portion be at least 38 bytes for 802.3 or 46 bytes for Ethernet
MAC ( Medium Access Control)
25-47 位 組織唯一標誌符(organizationally unique dentifier,OUI).
OUI 是由 IEEE 分配給每個組織. 組織按高到低的順序分配 1 個唯一的全域位址給每個網卡以保證不會有重複的編號.
第 47 位 individual/Group(I/G)位,
當 I/G 位為 0 的時候,我們可以設想這個位址是 MAC位址的實際位址可以出現在 MAC 頭部資訊;
當 I/G 位為 1 的時候,我們可以設想它為廣播或多播.
第 46 位 G/L 位,也叫 U/L 位.
當這個位為 0 的時候代表它是由 IEEE 分配的全域地址;
當這個位為 1 的時候,代表本地管理地址(例如在 DECnet 當中)
訂閱:
意見 (Atom)